Secure access to your organization’s critical resources is a top priority in today’s cloud-first world. With digital transformation accelerating and teams working remotely, the need for robust access management solutions has never been greater. HashiCorp Boundary Enterprise Crack is a powerful, cloud-native solution designed to simplify and secure access across hybrid and multi-cloud environments.
What is HashiCorp Boundary Enterprise?
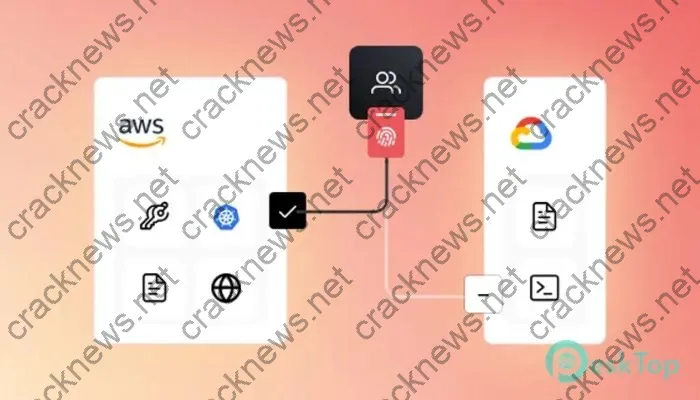
HashiCorp Boundary Enterprise is the enterprise version of the open-source Boundary project, offering advanced features and commercial support for production deployments. At its core, Boundary provides a centralized access management solution that enables you to control who can access what resources and from where.
Some key capabilities of Boundary Enterprise include:
- Access Control: Granular access controls based on user identity, resource attributes, and contextual information like source IP address or device posture.
- Audit Logging: Comprehensive audit logging and session recording for compliance and security monitoring.
- Session Management: Secure, short-lived credential injection and session management for various access methods like SSH, RDP, Kubernetes, and more.
Boundary is designed to work seamlessly across hybrid and multi-cloud environments, making it a flexible solution for modern, distributed architectures.
Top Features of Boundary Enterprise
Centralized Access Management
With HashiCorp Boundary Enterprise Free download, you can centrally manage and control access to your organization’s resources, whether they reside on-premises, in the cloud, or across multiple cloud providers. The unified management console simplifies the process of defining and enforcing access policies, reducing the risk of misconfiguration and ensuring consistent controls across all environments.
Secure Credential Injection
One of the standout features of Boundary Enterprise is its secure credential injection capability. Instead of sharing sensitive credentials like passwords or private keys, Boundary generates short-lived credentials on-demand, reducing the risk of credential exposure and enhancing security.
See also:
Comprehensive Audit Logging
Boundary Enterprise provides detailed audit logs and session recordings, enabling you to meet compliance requirements and gain visibility into user activities. This feature is particularly valuable for organizations operating in regulated industries or those with stringent security protocols.
Easy Integration
Boundary Enterprise integrates seamlessly with existing identity providers (IdPs), allowing you to leverage your existing user directories and authentication mechanisms. Additionally, its pluggable authentication methods enable you to extend Boundary with custom authentication workflows as needed.
How Boundary Works
At a high level, Boundary follows a simple architecture consisting of three main components:
- Controllers: Responsible for managing access policies and generating credentials.
- Workers: Facilitate secure connections between clients and target resources.
- Clients: Boundary’s lightweight clients initiate access requests and establish connections.
When a user requests access to a resource, the Boundary client authenticates with the controller, which then generates short-lived credentials and establishes a secure connection to the target resource via a worker.
Key Benefits of Using Boundary Enterprise
Improve Security Posture
HashiCorp Boundary Enterprise Serial Key helps organizations enhance their security posture by implementing least privilege access controls and preventing credential exposure. By enforcing granular access policies and generating short-lived credentials, Boundary reduces the risk of unauthorized access and minimizes the potential impact of a security breach.
Increase Operational Efficiency
With Boundary Enterprise’s centralized management console and automated credential management capabilities, organizations can streamline their access management processes and reduce the operational overhead associated with managing and distributing credentials manually.
Support Cloud Agility
Boundary’s cloud-native design and simple multi-cloud deployment make it an ideal solution for organizations embracing cloud agility. Whether you’re operating in a single cloud or across multiple cloud providers, Boundary Enterprise enables seamless access management without compromising security or introducing complex infrastructure dependencies.
Getting Started with Boundary Enterprise
To get started with HashiCorp Boundary Enterprise Crack, you’ll need to ensure your environment meets the following system requirements:
- Operating Systems: Boundary supports various operating systems, including Linux, macOS, and Windows.
- Hardware: Boundary has minimal hardware requirements, making it suitable for deployment on a wide range of infrastructure, from physical servers to cloud instances.
- Dependencies: Boundary relies on a few external dependencies, such as a database (PostgreSQL or MySQL) and a storage backend (S3, GCS, or Azure Blob Storage) for persistent data storage.
Once installed from our site, you’ll need to configure Boundary by defining your access policies, integrating with your identity provider, and setting up the necessary authentication methods. HashiCorp’s documentation provides step-by-step guides to help you through this process.
If you’re currently using the open-source version of Boundary, HashiCorp offers migration tools and documentation to help you seamlessly transition to the enterprise edition.
Best Practices and Use Cases
Boundary Enterprise can be leveraged across a wide range of use cases, including:
- Remote Access: Secure access for remote employees, contractors, and third-party vendors.
- DevOps and Infrastructure Access: Controlled access to production resources for developers and operations teams.
- Privileged Access Management: Manage and audit access to sensitive systems and resources.
- Cloud and Hybrid Environments: Consistent access management across on-premises, cloud, and multi-cloud environments.
To ensure optimal security and performance, HashiCorp recommends following best practices, such as:
- Principle of Least Privilege: Grant users only the minimum access necessary to perform their tasks.
- Multi-factor Authentication: Implement multi-factor authentication (MFA) for added security.
- Monitoring and Alerting: Set up monitoring and alerting to detect and respond to potential security incidents.
- Regular Policy Reviews: Periodically review and update your access policies to align with changing business requirements and security standards.
See also:
Support and Resources
HashiCorp offers various support options for HashiCorp Boundary Enterprise Activation Key users, including:
- Commercial Support: Paid support plans with different service levels, providing access to HashiCorp’s expert support team.
- Community Support: Free community support through forums, mailing lists, and online documentation.
Additionally, HashiCorp provides comprehensive training and certification programs to help users and organizations upskill and become proficient in using Boundary Enterprise effectively.
As the Boundary project continues to evolve, HashiCorp’s roadmap includes exciting new features and enhancements, such as improved integration with other HashiCorp products, enhanced identity federation capabilities, and support for additional access protocols.
Conclusion
HashiCorp Boundary Enterprise Crack is a robust, cloud-native access management solution that enables organizations to securely control and manage access to their critical resources across hybrid and multi-cloud environments. With its centralized management console, secure credential injection, comprehensive audit logging, and seamless integration capabilities, Boundary Enterprise empowers organizations to enhance their security posture while increasing operational efficiency.
This tool is really impressive.
It’s now much easier to finish projects and organize data.
It’s now far more intuitive to finish tasks and track content.
I really like the upgraded dashboard.
The new updates in release the newest are extremely awesome.
It’s now far easier to get done tasks and organize content.
The latest features in release the latest are incredibly helpful.
I would strongly endorse this program to anybody looking for a robust product.
I would highly suggest this application to anybody wanting a high-quality product.
The performance is significantly improved compared to the original.
The latest enhancements in update the latest are so helpful.
The loading times is significantly enhanced compared to the previous update.
It’s now a lot simpler to do tasks and track content.
I really like the new UI design.
The latest enhancements in update the newest are really awesome.
The speed is so much enhanced compared to last year’s release.
It’s now a lot simpler to do tasks and track content.
It’s now far easier to do projects and manage content.
I would strongly recommend this tool to anyone needing a robust product.
I would highly recommend this program to professionals looking for a powerful solution.
I appreciate the upgraded layout.
I would absolutely suggest this program to anyone looking for a high-quality solution.
The program is absolutely impressive.
It’s now far simpler to finish jobs and track content.
The responsiveness is so much improved compared to last year’s release.
The program is really amazing.
The loading times is significantly improved compared to the original.
This software is absolutely impressive.
I would strongly recommend this tool to anybody looking for a robust solution.
This platform is definitely impressive.
I really like the improved UI design.
It’s now much easier to get done jobs and manage information.
I absolutely enjoy the new workflow.
It’s now much easier to do work and track data.
The latest updates in update the newest are really awesome.
It’s now much more user-friendly to do work and manage data.
The platform is definitely amazing.
The responsiveness is a lot enhanced compared to older versions.
I would strongly suggest this software to anybody wanting a robust solution.
I would definitely endorse this application to professionals wanting a high-quality product.
I would strongly endorse this program to professionals wanting a high-quality product.
The speed is significantly faster compared to the previous update.
I would highly suggest this application to anybody needing a robust solution.
The responsiveness is so much faster compared to last year’s release.
It’s now much more user-friendly to do jobs and organize data.
I would absolutely endorse this application to anybody needing a high-quality solution.
It’s now much simpler to complete work and manage content.
I would definitely endorse this program to anyone looking for a top-tier product.
I would absolutely endorse this program to anybody needing a high-quality solution.
The responsiveness is a lot enhanced compared to older versions.
It’s now far more user-friendly to complete tasks and manage content.
I would absolutely suggest this application to anybody looking for a robust solution.
The recent enhancements in update the latest are really helpful.
The recent capabilities in version the latest are incredibly great.
The latest updates in update the latest are so helpful.
The latest capabilities in update the latest are so helpful.
The loading times is significantly improved compared to the original.
I would definitely suggest this software to anyone looking for a top-tier platform.
I appreciate the enhanced dashboard.
It’s now far easier to get done projects and manage data.
It’s now far simpler to get done tasks and manage data.
The speed is a lot improved compared to last year’s release.
The speed is significantly better compared to older versions.
The recent enhancements in update the newest are really great.
The recent functionalities in version the newest are really great.
I would highly endorse this application to anybody needing a top-tier solution.
The responsiveness is so much enhanced compared to the original.
The loading times is significantly improved compared to the original.
It’s now much easier to get done tasks and track information.
It’s now a lot simpler to finish tasks and organize content.
The tool is really amazing.
The recent capabilities in release the latest are really great.
The latest features in release the newest are incredibly helpful.
The speed is a lot improved compared to last year’s release.
It’s now a lot more user-friendly to do tasks and track information.
It’s now much easier to complete projects and manage content.
The program is really fantastic.
I would absolutely endorse this tool to anyone needing a high-quality product.
The recent features in release the newest are really cool.
It’s now far more intuitive to finish jobs and organize information.
I would absolutely endorse this software to anyone wanting a powerful solution.
It’s now far easier to complete projects and track data.
The latest functionalities in version the newest are incredibly awesome.
It’s now far more intuitive to complete work and track data.
I love the improved layout.